Writing secure SQL queries is crucial to prevent vulnerabilities such as SQL injection. Using prepared statements is one of the best practices to ensure that your SQL queries are safe.
Here’s a guide on how to do this effectively.
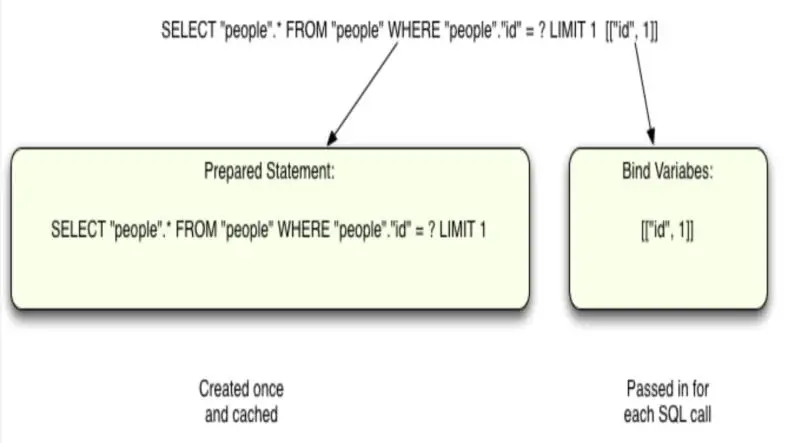
What are Prepared Statements?
Prepared statements are a feature of many database management systems (DBMS) that allow you to define a SQL query template and then execute it with specific parameters. This separation of SQL logic and data helps protect against SQL injection.
Benefits of Prepared Statements
- Security: Automatically escapes input parameters, reducing the risk of SQL injection.
- Performance: The SQL query plan can be reused, which may improve performance for repeated queries.
- Maintainability: Clearer separation of query logic and data.
How to Use Prepared Statements
Here’s how to implement prepared statements in different programming languages:
1. PHP with PDO
try {
$pdo = new PDO('mysql:host=localhost;dbname=testdb', 'username', 'password');
$pdo→setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION);
// Prepare the SQL statement
$stmt = $pdo→prepare('SELECT * FROM users WHERE email = :email');
// Bind parameters
$stmt→bindParam(':email', $email);
// Execute the statement
$email = 'user@example.com';
$stmt→execute();
// Fetch results
$results = $stmt→fetchAll(PDO::FETCH_ASSOC);
}
catch (PDOException $e) {
echo 'Connection failed: ' . $e→getMessage();
}
2. Python with SQLite
import sqlite3
# Connect to the database
conn = sqlite3.connect('example.db')
cursor = conn.cursor()
# Prepare the SQL statement
cursor.execute('SELECT * FROM users WHERE email = ?', (email,))
# Fetch results
results = cursor.fetchall()
# Close the connection
conn.close()
3. Java with JDBC
import java.sql.Connection;
import java.sql.DriverManager;
import java.sql.PreparedStatement;
import java.sql.ResultSet;
public class Main {
public static void main(String[] args) {
String url = "jdbc:mysql://localhost:3306/testdb";
String user = "username";
String password = "password";
try (Connection conn = DriverManager.getConnection(url, user, password)) {
String sql = "SELECT * FROM users WHERE email = ?";
PreparedStatement pstmt = conn.prepareStatement(sql);
pstmt.setString(1, "user@example.com");
ResultSet rs = pstmt.executeQuery();
while (rs.next()) {
// Process results
}
}
catch (Exception e) {
e.printStackTrace();
}
}
}
General Tips
- Always use parameterized queries: Never directly embed user input into SQL queries.
- Validate and sanitize inputs: While prepared statements are safe, it’s good practice to validate data formats.
- Use appropriate data types: Bind parameters with the correct types to avoid unexpected behavior.
- Limit database privileges: Ensure that your database users have only the permissions necessary to perform their tasks.
Prepared statements are an essential tool for writing secure SQL queries. By using them consistently across your applications, you can significantly reduce the risk of SQL injection attacks and enhance the overall security of your database interactions.
Thanks for reading the article, for more Science and Technology related articles read and subscribe to peoples blog articles.